More and more inexperienced users are setting up hosting accounts in an attempt to launch а successful online project. The first steps can be a bit intimidating simply because of the large number of technical terminology and seemingly endless tasks.
SSH is an excellent example of a piece of technology that causes a lot of confusion among newbies. The mission of today’s guide is to clear up some of the pressing questions that surround this management solution.
But first things first…
What is SSH?
SSH stands for Secure Shell, and it’s a communication protocol that creates a connection between two computers. But how does it help you manage your website on your hosting account? It’s pretty simple.
Your site is hosted on a server – essentially, a powerful computer located in a data center that may be thousands of miles away from you. If you need to make any changes to your website, you don’t go to the data center and manage the server from there. You connect to it from your home or office.
This is where Secure Shell comes into play.
While other protocols also let you manage your account remotely, SSH excels when it comes to security.
But how does it create such a safe environment exactly?
How Does SSH Work?
SSH traces its roots back to 1995 when Tatu Ylönen, a Finnish researcher, was fighting off a password sniffing attack targeting Helsinki University’s network. Popular communication protocols at the time established a plaintext connection between clients and servers. This means they transmitted all the data, including usernames and passwords, in a human-readable format.
This kind of environment made it easy for hackers to intercept the login credentials and infiltrate the targeted network. Ylönen realized that by using encryption, he could create a much more secure connection. The idea was further developed by the Internet Engineering Task Force, which released version 2 of the protocol in 2006.
SSH-2 is even safer than its predecessor, thanks to a combination of symmetric, asymmetric encryption, and hashing. Understanding the different encryption techniques is crucial when understanding how SSH works.
Symmetric encryption
In symmetric encryption, your computer uses a cryptographic key to turn the information you’re sending (e.g., a command you’re trying to execute on the server) into a jumbled string of letters and digits.
Upon reception, the server uses an identical key to decrypt the command. Your computer and the server follow a predetermined key exchange algorithm to generate the symmetric key. They do it independently, and they never share the key with a third party.
Asymmetric encryption
Asymmetric encryption is a bit more complex. Upon establishing a connection, the client and the server generate public/private key pairs. The public keys, as their name suggests, are readily available. The private keys, however, are only stored on the two communicating machines.
In asymmetric encryption, you use the public key to encrypt the data and the private one to decrypt it.
When you transmit a piece of information over an asymmetrically encrypted connection, your computer uses its public key to scramble your data and protect it while in transit. The server will be able to decrypt it only if it has your machine’s private key.
Hashing
Hashing is a rather different concept altogether. Similar to symmetric and asymmetric encryption, it’s a function that scrambles up information so that it’s impossible for attackers to intercept and read it.
Every message that passes through the hashing algorithm produces a unique string called a hash value. However, there is no key to decrypt the data and restore it in a human-readable format. It’s a one-way cryptographic function that doesn’t allow for the retrieval of the original information.
How does SSH work with these encryption techniques?
Establishing an SSH connection to your server takes no more than a couple of seconds, but under the surface, there’s quite a lot going on.
First, you have the session encryption negotiation phase. While it is in progress, your computer and the server each present a list of supported encryption and hashing algorithms, and the two machines agree upon which one they’ll use.
Next, your computer and the server generate public-private key pairs. The server then uses your public key to encrypt a challenge and send it back to you. It utilizes asymmetric encryption, meaning your machine can decrypt the challenge only if it has your private key.
If that’s the case – the SSH session begins.
Your computer and the server now share public pieces of data and use a predetermined key exchange algorithm to create a symmetric encryption key. This one will be used to protect the flow of information between the two machines. The key exchange algorithm remains unknown, so nobody else can generate the encryption key.
When the secure connection is established, your computer and the server use a predetermined hashing algorithm to create unique Hash-based Message Authentication Codes (or HMACs) for every single message that passes between the two machines. Each authentication code is calculated based on the message’s contents, the symmetric encryption key, and the packet sequence number. HMACs are there to ensure the messages’ authenticity and guarantee they’ve not been tampered with.
The final step is authenticating the user. The server will either ask you for your login credentials or use cryptographic keys to verify your identity before letting you in.
How to Set Up SSH on Your VPS?
How you’re going to go about accessing VPS via SSH depends mostly on your hosting account. For example, with a self-managed virtual server, SSH is enabled by default, and you likely have root access.
With a managed VPS solution, things are a bit different.
Usually, you get a point-and-click interface through which you can create individual accounts, modify their permissions, and enable their SSH access.
There are more than a few web hosting control panels, each with its own Graphical User Interface (or GUI), so the exact steps you need to take depend on the management platform.
If, for example, your hosting provider uses cPanel/WHM, you’ll need to do the following:
- Log into WHM
- From the menu on the left, locate the Account Functions section and select Modify an Account
- Find the account you want to change and click Modify
- Scroll down to the bottom of the page and select the checkbox that says Shell Access
- Click Save
- A popup will ask you whether you want to update the package and make SSH access available for all users in this group. Select the most appropriate option and click Proceed
Enabling SSH access for individual accounts is also possible if you use one of ScalaHosting’s SPanel VPSs.
Here are the steps:
- Log into the SPanel Admin Interface
- Go to Manage SSH Access from the menu on the left
- Find the account you need and use the toggle switch next to it to enable and disable SSH access
SSH was developed out of the necessity for a more secure communication protocol, and the complex cryptography it uses shows that security is at its very core. Nevertheless, if you have a self-managed server with a default configuration, there are a couple of steps you can take to protect your machine even further.
Changing the default SSH port is the first one. It’s common knowledge that SSH works via port 22 by default, and hackers who want to brute-force their way into the server usually aim their attacks at it. Switching to another free port is often good enough to stop them or at least slow them down.
To thwart more targeted attacks, you can use an SSH client to generate a public and private key pair for authentication purposes. The default user/pass mechanism is what most of you are probably used to, but cryptographic keys offer a lot more security.
SSH Use Cases
Most site admins use SSH for command execution. Unix-based operating systems like Linux and macOS can connect to a remote server via SSH directly from the Terminal. After a 2018 update, accessing your server via SSH is also possible through Windows PowerShell, so users of the Microsoft OS no longer need a separate client application.
There’s no GUI option available when it comes to managing a server via SSH. If you want to use the protocol – you’ll need to get comfortable with a command-line interface tool. If you’re not, you may find SSH far too complicated, especially given the wide range of GUI-based management platforms.
However, different projects have different needs, and some website administrators rely on tools that can only operate via SSH. What’s more, many experienced users find it easier and quicker to manage their websites via the console.
Command execution is far from SSH’s only application, though. The protocol can be used for tunneling ports and connections and securing pretty much any network service you can think of. The best-known example of a service that uses SSH is SFTP.
ScalaHosting and SSH Access
At ScalaHosting, we want to make sure our services fit the needs of as many users as possible. This is why SSH access is available for most of our clients.
If you have a shared hosting package and need SSH access, you can ask our technical support experts to set it up for you in no time.
With a self-managed VPS, you’ll get root access and instructions on how to log into your server immediately after we set it up. And if you want to leave the server management to us – you can get a managed VPS with a GUI-based control panel (either WHM/cPanel or SPanel).
With it, you’ll decide for yourself who gets SSH access and who doesn’t.
With SSH access enabled, you can use your operating system’s command-line interpreter to log in. The initial command specifies the protocol, the user account, and the host. For example, if you want to access a server with a hostname domain.com with the account with a username user, you’ll enter the following command.
ssh user@domain.com
If you use SPanel, you’ll need to add -p 6543 to the end because our VPS solutions use custom SSH port for additional security.
After you press Enter, the server will ask you for your account’s password, and if you provide the correct details, it will log you in.
However, in addition to the standard login credentials, you can also use SSH keys to access and manage your SPanel VPS. The easiest way to generate and use SSH keys is with a client application.
PuTTY is one of the most popular SSH clients, so we’ll use it for our example. It’s free to download and use, and it’s bundled with PuTTYgen – an easy-to-use tool for generating SSH key pairs.
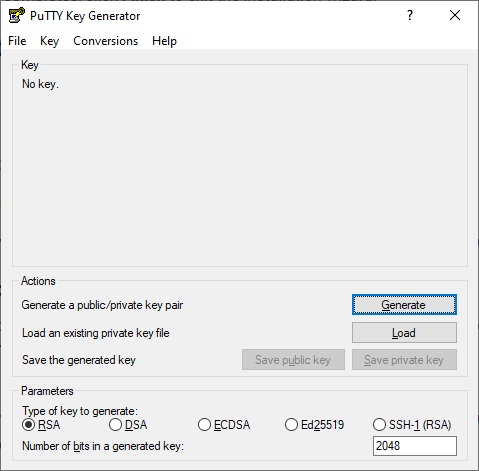
To create a new key pair, click Generate,and shake the mouse cursor inside the gray field for a bit. The keys will be ready within a couple of seconds, and thanks to your random mouse movements, they will be genuinely unique.
PuTTYgen lets you create different types of keys, but you most likely don’t need to waste time researching them all. The default parameters work perfectly well for standard SSH connections.
At this point, you can assign a passphrase for additional security. If you do, you’ll need to enter it every time you use your SSH key to log in to your server. When ready, click the Save private key button to store it on your computer’s hard drive.
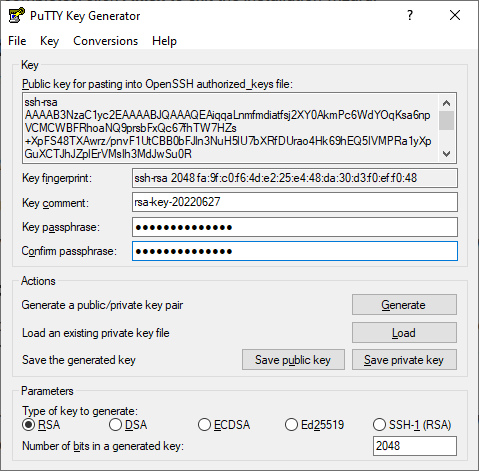
PuTTYgen also lets you save the public key as a local file, but you rarely need to because your next step is to upload it to your server. Even if you don’t proceed immediately, you can always access the public key by opening PuTTYgen and loading the private key.
You need to save the public key to the ~/.ssh/authorized_keys file on your SPanel server. Here’s how to do it.
Log in to your account via SSH using your username and password. You’ll want to make sure you’re in the correct directory. The command is:
$ cd ~
To double-check, you can also run pwd. The output should be /home/[your username].
First, you need to create the .ssh folder and the authorized_keys file. You can start with the following command:
$ mkdir .ssh
If you get an error stating that the folder already exists, this most likely means that the server is configured to work with at least one public key. Whatever the case, your next step is to add your public key to the authorized_keys file. The command is:
$ nano .ssh/authorized_keys
This opens the GNU nano text editor. If the authorized_keys file already exists, you’ll see its contents. If you’re creating it right now, GNU nano will display a blank page.
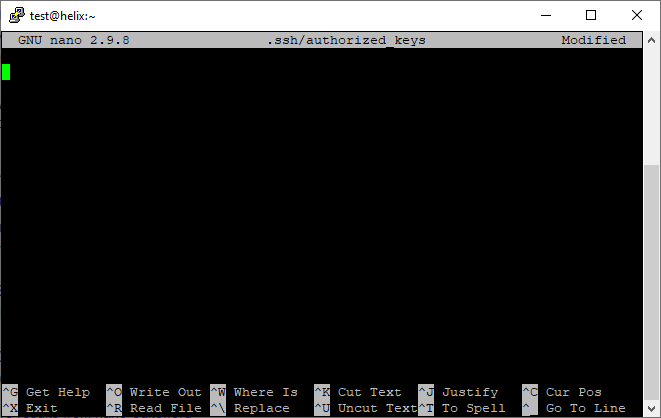
It’s time to go back to the PuTTYgen tool and copy the public key from the field at the top.
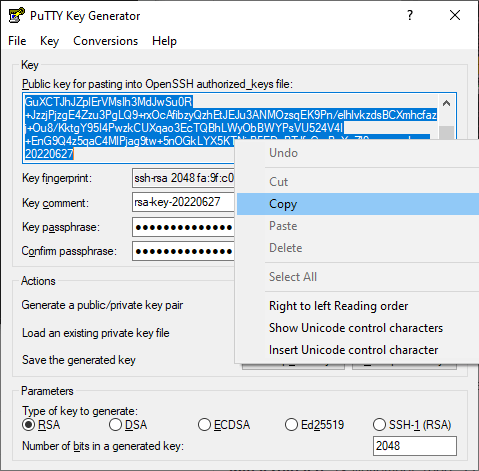
Paste it into the GNU nano editor (the easiest way is to right-click inside the editor), and make sure you save the changes when exiting.
The server has your public key now. However, you need to set the correct permissions and ownership if the file is to work. The commands you’ll use are:
$ chmod 700 .ssh
$ chmod 600 .ssh/authorized_keys
$ chown $[your username]:[your username] .ssh -R
The only thing left to do is configure PuTTY to work with the private key.
First, open the client and go to SSH > Auth. Use the Browse button to select the private key you previously saved on your hard drive.
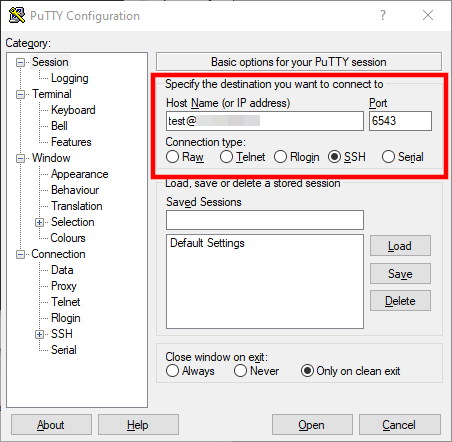
Next, go to the Session menu and enter the correct details for your server. You can save them as a session for later use. That way, you won’t need to locate and select your private key whenever you want to log in.
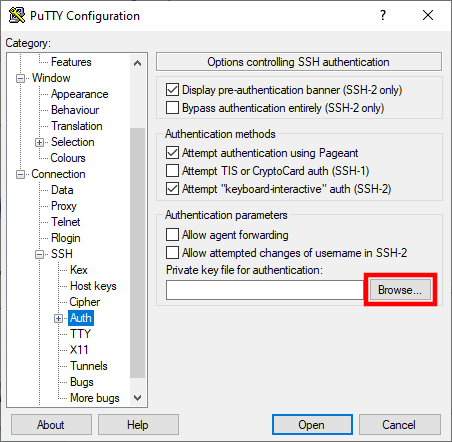
Finally, click Open to connect to your SPanel server via SSH.
Conclusion
SSH may seem like a rather old-fashioned way of managing a hosting account, especially for people who are used to point-and-click control panels. The protocol has indeed been around for quite a while now, and it’s not the most novice-friendly way of managing a website.
This doesn’t make it any less powerful, though.
Once you get familiar with the environment and commands – you’ll forget there was any other way of doing things.


FAQ
Q: How do I connect to my server via SSH?
A: You can connect to your server via SSH using either your operating system’s command-line interface or a standalone client application. You’ll use the login credentials provided by your host, and the first command you’ll need to enter is:
ssh [username]@[the server’s IP]
You will then be asked for your password, and after successful authentication – you will be able to start working on your server.
Q: What are SSH keys used for?
A: In addition to the traditional user/pass authentication method, SSH allows for the use of cryptographic keys for confirming the user’s identity. The underlying cryptography makes SSH keys much more secure than regular login credentials.
Q: Is SSH available on Windows?
A: In the past, Windows users could only establish SSH connections through standalone client applications like PuTTY. However, in 2018, Microsoft released an update that integrated SSH functionality into Windows PowerShell, so if your system is up-to-date – you can log into your server without installing additional applications.
What is a VPS – Everything you need to know!