
Best WordPress Plugins To Increase Sales In 2025
In the past few years, numerous retailers and shops have shifted to online and ecommerce channels, and it seems the …

In the past few years, numerous retailers and shops have shifted to online and ecommerce channels, and it seems the …
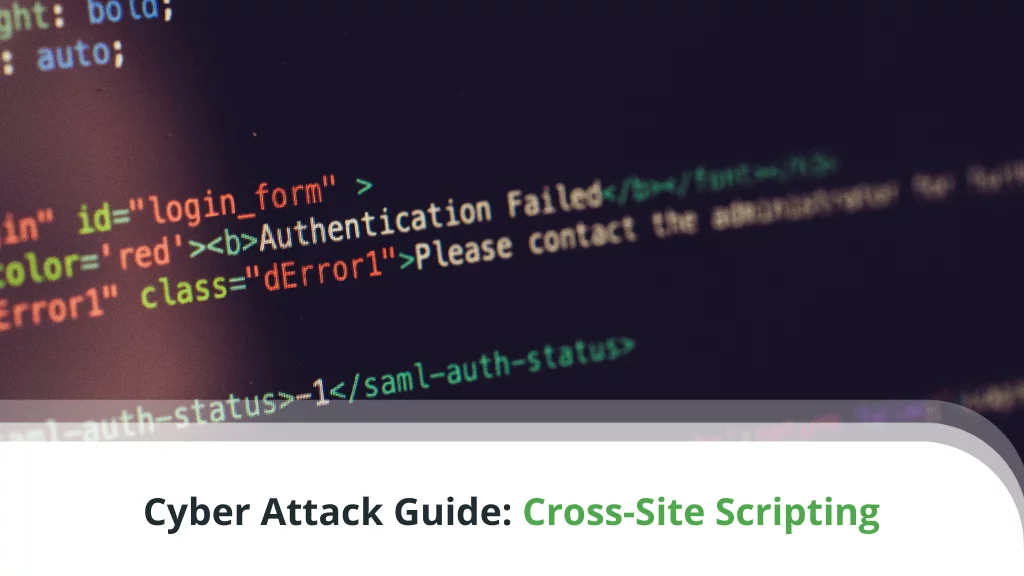
Cross-site Scripting (XSS) attacks have been around pretty much for as long as we’ve had web applications that help site …

Those of us who remember the days when the internet wasn’t quite as ubiquitous, know just how much more difficult …

Joomla is a Content Management System (CMS) designed to help users build and run websites that serve large amounts of …

Over the years, we’ve seen far too many malware attacks that have had a genuinely devastating worldwide impact. For example, …

Currently, there are around 200 million active websites, and very few of them consist solely of the static HTML pages …
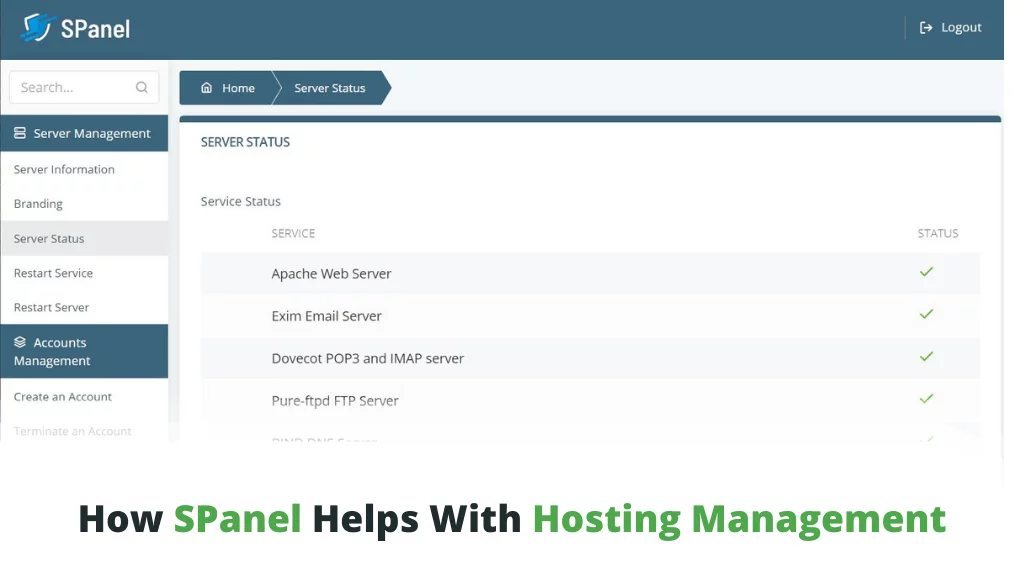
Managing web hosting accounts can be a little confusing. Most of us start out using shared hosting, which is simple …

Docker was launched in late-2013, which, compared to some of the other technologies web application developers use, isn’t that long …

Web hosting comes in several different forms – from shared hosting for small projects to dedicated server hosting reserved primarily …

The concept of phishing finds its way back in the 1980s, and the term has been in broad circulation since …
Linux Virtual Private Server (VPS) hosting is an incredibly powerful and flexible option for growing businesses and ecommerce projects. Yet, …

Some people use the internet to watch cat videos and communicate with friends. Others depend on it for their livelihood. …