CSF and LFD often come pre-installed to enable you to keep tabs on activities happening on your servers. They send valuable notifications to help you keep track of potentially important events on the server.
The feature enables users to detect server events that might be indicative of security issues. Some of these notifications could be difficult to decipher by the uniformed. So this article guides you on everything you need to know about CSF and LFD and their common notifications.
Understanding CSF and LFD
CSF and LFD offer features that help users secure their servers. Let’s examine quickly what these terms mean and what they do.
ConfigServer Security and Firewall (CSF)
CSF, short for ConfigServer Security and Firewall, is a Stateful Packet Inspection (SPI) firewall that helps keep servers secure. Stateful inspection analyzes packets down to the application layer, unlike static inspection that checks only the packet’s header, which leaves a tiny window for attackers to exploit.
The stateful firewall uses SPI to determine the packets to allow through the firewall. ConfigServer Security and Firewall provides an intuitive web-based interface for managing your server firewall settings, though you can also manage the settings via Secure Shell (SSH).
The firewall helps users to:
- Control traffic to their server space by closing all connections and allowing them to open the connection to receive traffic
- Prevent DDOS attack by closing outgoing ports, allowing only those authorized for outgoing traffic
- Track network connections, notifying them of those that made a suspicious number of failed attempts
Only root users (system admins) can access and manage CSFs.
Login Failure Daemon (LFD)
Login Failure Daemon is a critical component of the CSF process. It periodically checks for potential threats against a server, such as brute force login attempts, and blocks the IP address to protect the server from inbound attacks.
Brute force attackers often guess usernames and passwords, thereby generating many authentications and login failures within a short time. LFD scans the latest authentication log files to identify these patterns. If found, the daemon responds quickly by using CSF to block the offending IP address.
LFD is a daemon. It works as a background process, monitoring log files to respond immediately to threats.
Common CSF and LFD Notifications
Enabling email alerts for LFD, though this is on by default, lets you receive notifications when the daemon blocks an IP address. Here’s a quick rundown of the common CSF and LFD notifications.
IP Blocks Alerts
LFD sends email notifications any time it blocks an IP address. This alert is active by default; however, you can disable it if you’re confident your firewall configuration only blocks the IPs you want blocked.
Too many notifications might distract your attention from other important things. Some of the reasons LFD blocks IP addresses include:
Login Failures
The LFD blocks an IP address when it fails too many login attempts within a short space and sends you an email alert that looks thus:
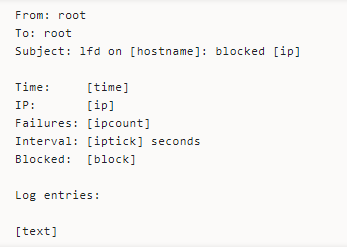
Temp to Perm Block
LFD has a feature that lets users enable a trigger that permanently blocks an IP address after stopping it temporarily for a certain number of times over a specified period.
You’d receive an LFD alert whenever this happens. The email alert looks thus:
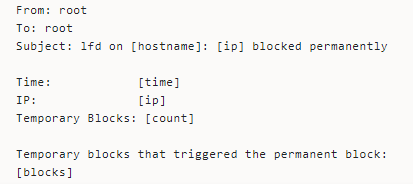
Too Many Connections
Simultaneous connections from the same IP could cause the daemon to block the IP. Besides being indicative of a DDOS attack, this type of connection could also cause load issues.
Here’s how the email looks.
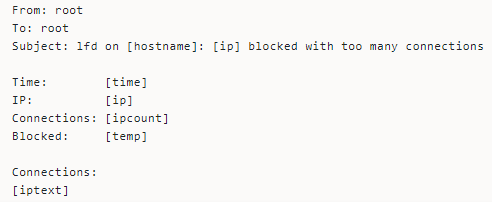
Other reasons the daemon blocks IP addresses include:
- Too many attempted connections to closed ports
- When an IP address tries to log into the same email account more than expected
The LFD can also block an entire netblock and the associated IP addresses due to previously blocking a lot of its IPs many times within a specific interval.
Successful Logins Alerts
The daemon sends email notifications for successful logins. This notification helps system admins track the people logging into their servers to ensure only authorized users access the server.
Some of the login alerts LFD include:
Port Knocking
LFD notifies users when people access the server using a port knocking sequence—a technique that externally opens ports the firewall keeps closed by default. Port knocking helps keep a server secure by closing firewall ports, even those available for use.
Network administrators use the authentication method to control access to a server or other network devices behind a firewall. LFD can detect when a user gains access via the method and sends you an alert.
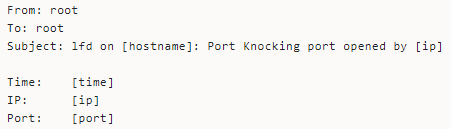
Secure Shell Access (SSH)
SSH allows users to access a server as if they are physically in front of the server. LFD sends notifications when a user successfully logs in to the server via SSH.
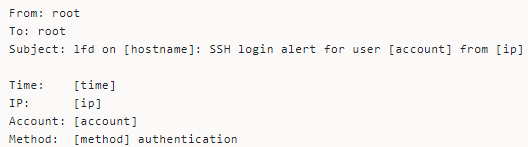
LFD also sends successful login alerts for:
- Logins to WHM or cPanel
- When someone accessed the server using the SU command—the substitute user command helps a user execute commands with the privileges of another user account.
- If a user logins via the CSF user interface.
Excessive Resource Usage Alerts
LFD watches the running processes to detect if they are using too many resources, and you can configure what counts as too many for some of the resources.
The notification text, by default, looks thus:
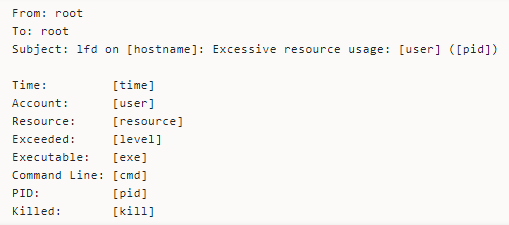
Here’s the meaning of some of the placeholders:
- PID shows the Process ID
- Time signals when LFD detected the process as using too many resources
- Resources point the resource the process seems to be exceeding
- Exceeded shows how much of the resources the daemon detected the process of using
- Executable logs the executable the process is running from
- Killed indicates whether or not LFD attempted to kill the process
Email Script Alerts
LFD watches the mail log to detect emails with scripts. It notifies you when this activity happens repeatedly. You might get an email showing the scripts and the number of emails involved.
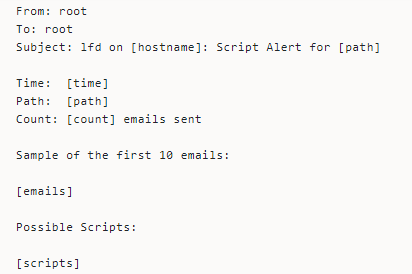
LFD guesses the likely email script, so the email alert might report an inaccurate script.
Excessive Processes Alerts
The daemon also watches whether a user is running numerous processes simultaneously. If it detects excessive processes, the daemon sends a notification letting you know that a user runs more processes than the configured threshold.
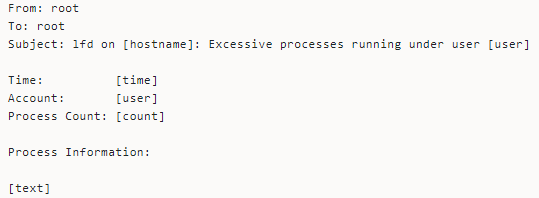
Excessive processes could be indicative of server security or resource issues.
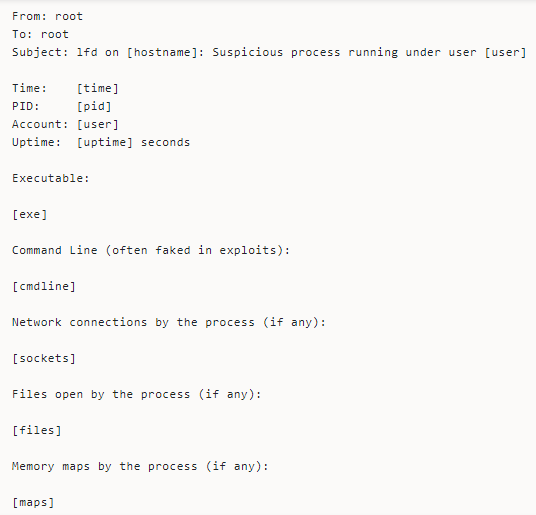
Suspicious Process Alerts
Enabling Process Tracking examines all running processes for suspicious, deleted executable files or open network ports. It sends an email notification when it identifies a suspicious process running on the server.
You might receive this kind of email alert.
System Integrity Alert
LFD comes with features that watch for changes in specific system files, helping detect compromised files. The daemon also sends alerts when routine system updates change the files.
The email notification looks thus:
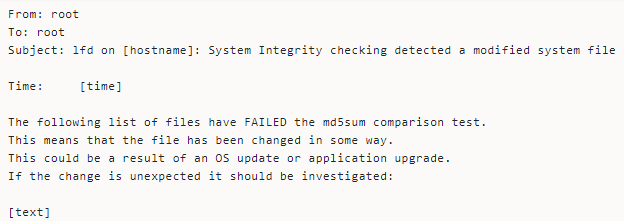
Always check your server log when you receive this alert to determine if the file changes are due to system updates, intentional changes, or suspicious activity.
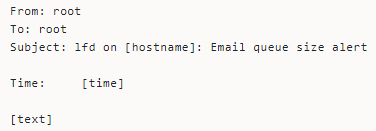
Email Queue Size Alerts
Whenever you send emails, the SMTP server places the email on a queue where they await processing. Often, the server delivers the email immediately without it accumulating in the email queue.
Some of the common things causing email accumulation are indicative of security issues. So, the LFD watches the length of the email queue and sends notifications when too many emails accumulate in the queue.
Here’s how the email alerts look like:
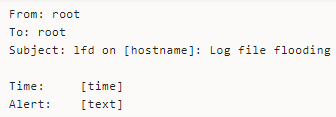
Log File Flooding Alerts
LFD relies heavily on various server logs to watch server activities and could become ineffective if the logs get flooded with too many similar lines in a row. The daemon sends notifications whenever it detects log file flooding.
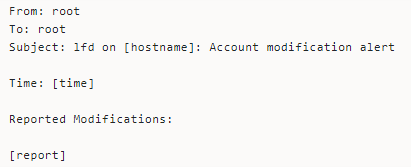
Account Modification Alerts
LFD sends email alerts for certain types of account modification and the detected changes. The alert helps users keep a tab on account modifications and take immediate actions to address suspicious activity.
The text of the notification, by default, looks thus:
Disabling All LFD Notifications Via the Command Line
Enabling all these alerts lets you take complete charge of your server security. However, you can deactivate all the LFD notifications.
- Take these steps to get it done via the command line.
- Log in via SSH to access your server remotely and open the CSF configuration file.
- Locate LF_PERMBLOCK_ALERT in the file and set the value to zero (0).
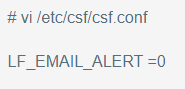
That’s it. Just restart the LFD and CSF services to enable the changes.
Wrapping It Up
Config Security Firewall with Login failure Daemon offers valuable features that help keep your server secure. And you could set up notifications to stay updated on the activities happening on your servers which helps you track all the events that could compromise the server.
You can switch off the notifications (or any of them) when you feel overwhelmed. Our support is always available to help when you need assistance.
