HTTP and HTTPS are the communication protocols we use for viewing a website in our browsers, but before we can do that, the website’s operator needs to upload some files to a server connected to the internet. For many years, the easiest and most convenient way to do this was through FTP (File Transfer Protocol). It’s still in use today, and considering the fact that the technology is close to 50 years old, this is quite an achievement, but FTP is starting to show its age.
Table of Contents:
- What is SFTP?
- Why should I use it?
- What can I do with it?
- The pros and cons of SFTP
- How to make it more secure?
- How to set up an SFTP connection with a VPS from ScalaHosting?
- Conclusion
The truth is, the experts who developed the File Transfer Protocol had nowhere near as many things to worry about as today’s website owners, and the problems were inevitable. Fortunately, there are enough people ready to ensure that there are solutions to these problems. These same people created SFTP (or SSH File Transfer Protocol).
What is SFTP?
Before we can answer this question, we need to go back to the beginning of SSH – the underlying communication technology that makes SFTP a great tool for a number of different tasks. SSH stands for Secure Shell, and it’s a remote administration protocol originally developed by a Finnish researcher called Tatu Ylonen as a way of mitigating the risk of password sniffing attacks. SSH’s first version was released in the 1990s, and alongside it, Ylonen also invested some work into a very early version of SFTP.
In the early 2000s, the Internet Engineering Task Force (IETF) started working on SSH-2 – a revised version of the protocol that eventually came out in 2006 and brandished much better security and quite a few new features. SSH-2 was not compatible with Tatu Ylonen’s version, which meant that when IETF took over, it also needed to overhaul the original incarnation of SFTP.
This proved to be a bit more complicated. At one point, there was a debate around whether or not SFTP is a protocol or an entire remote file system, and this delayed the development a bit. Eventually, however, in 2013, work on it was restarted, and the protocol has been in use ever since.
You might be wondering what the difference between SSH and SFTP is. SSH is a protocol that lets administrators manage and execute remote commands on the server. SFTP is an extension that allows them to upload, download, and manage files via the secure connection provided by SSH.
Why should I use it?
SFTP is sometimes referred to as “Secure File Transfer Protocol,” and you probably won’t be too surprised to learn that security is the main reason why you should use SFTP over the standard FTP. Here are the differences in more detail.
When connecting through a regular FTP connection, the client must be authenticated by the server, and, as you have probably guessed by now, this happens through a username and a password. These login credentials, as well as the rest of the information that is sent to the server, are transferred in plain text, which shouldn’t really be a surprise given the protocol’s age.
After all, back in the 1970s, the world wasn’t rife with hackers who could sniff through your communication, steal your passwords, or hijack your connection. Nowadays, however, things are a little bit different, which is why you need to make sure that your connection to the remote host is secure.
Because it’s based on SSH, SFTP uses cryptography to secure the data in transit and ensure that only authorized users are able to manage files on the server. First, the client and the host use a symmetric encryption algorithm to encrypt the connection. Symmetric encryption means that the data is encrypted and decrypted by one and the same key.
The key is created at the very beginning of the session using a key exchange algorithm, and the great thing about it is that the client and the server don’t transmit it or share it with any other parties. Instead, the key is calculated based on pieces of public data that are shared between the client and the server.
When the connection is secured, the SSH protocol commands the use of an asymmetric cryptographic algorithm to authenticate the client. Asymmetric cryptography is based on public-private key pairs. In this scenario, the public key encrypts the data, and the private one decrypts it. The server generates and encrypts a challenge and sends it to the client. If the client can decrypt it, it will prove that it has the private key and is authorized to communicate with the server.
From a user’s perspective, this whole mechanism is often hidden behind a simple username-and-password authentication mechanism. In other words, the steps you need to take in order to establish an SFTP connection are no more complicated than the ones you take during regular FTP sessions.
What can I do with it?
Plenty of people think that SFTP is the regular FTP run over a secure shell connection. This is not the case. The two protocols do share some functionalities like the ability to upload and download files and the remote management of directories, but SFTP gives clients a few additional capabilities. These capabilities include remote file removal, directory listings, and the ability to deliver more detailed metadata with the files.
The pros and cons of SFTP
SFTP is not the only means of securely transferring files between two connected computers. The Secure Copy Protocol (SCP), for example, also uses SSH to facilitate the copying of data between a client and a server, and the correct implementation of the rsync utility lets you achieve the same results. The limited functionality and the lack of support for some platforms, however, means that for most, these alternatives are not really viable. Usually, users have only two options to choose from – SFTP or FTPS.
FTPS is the implementation of the regular file transfer protocol over TLS (Transport Layer Security). It, too, uses cryptography to ensure that the connection between a client and a server is secure, and it’s definitely preferable to using the plain old FTP.
When compared to SFTP, however, it lags behind. Historically, configuring FTPS to work with firewalls has been a challenge, and in addition to all the extra functionalities, SFTP also has a few useful features like the ability to continue interrupted transfers. In the past, SFTP was mostly supported by command-line clients, which was a problem for less experienced users, but nowadays, applications with intuitive graphic interfaces like FileZilla can also establish SFTP connections.
SFTP’s only real disadvantage is that it’s more difficult to implement on the server side and is therefore not provided by all hosting providers.
How to make it more secure?
As you can see, your SFTP connection is backed by an extremely complex cryptographic mechanism, which is there to ensure that your data is secure. For the sake of usability, however, in most cases, you log in with your username and password, and this is where things could go very wrong.
A weak password can render all other security mechanisms completely useless in many scenarios, and SFTP communication, despite the complex cryptography it’s based on, is no exception. The stakes are pretty high as well.
The same credentials that log you in through SFTP also give you SSH access, which means that if hackers get their hands on them, they can remotely execute commands on the server. You must make sure that all users who have SSH and SFTP access use strong, unique passwords as well as up-to-date clients with all the security updates applied. Of course, there are server-side measures that need to be in place as well, but they’re the responsibility of the web host.
How to set up an SFTP connection with a VPS from ScalaHosting?
SSH and SFTP access is available on our cloud VPS hosting solutions, but because of the risks associated with everyone establishing SSH connections to the server, by default, it is disabled. You can easily enable it through SPanel, our all-in-one hosting management platform.
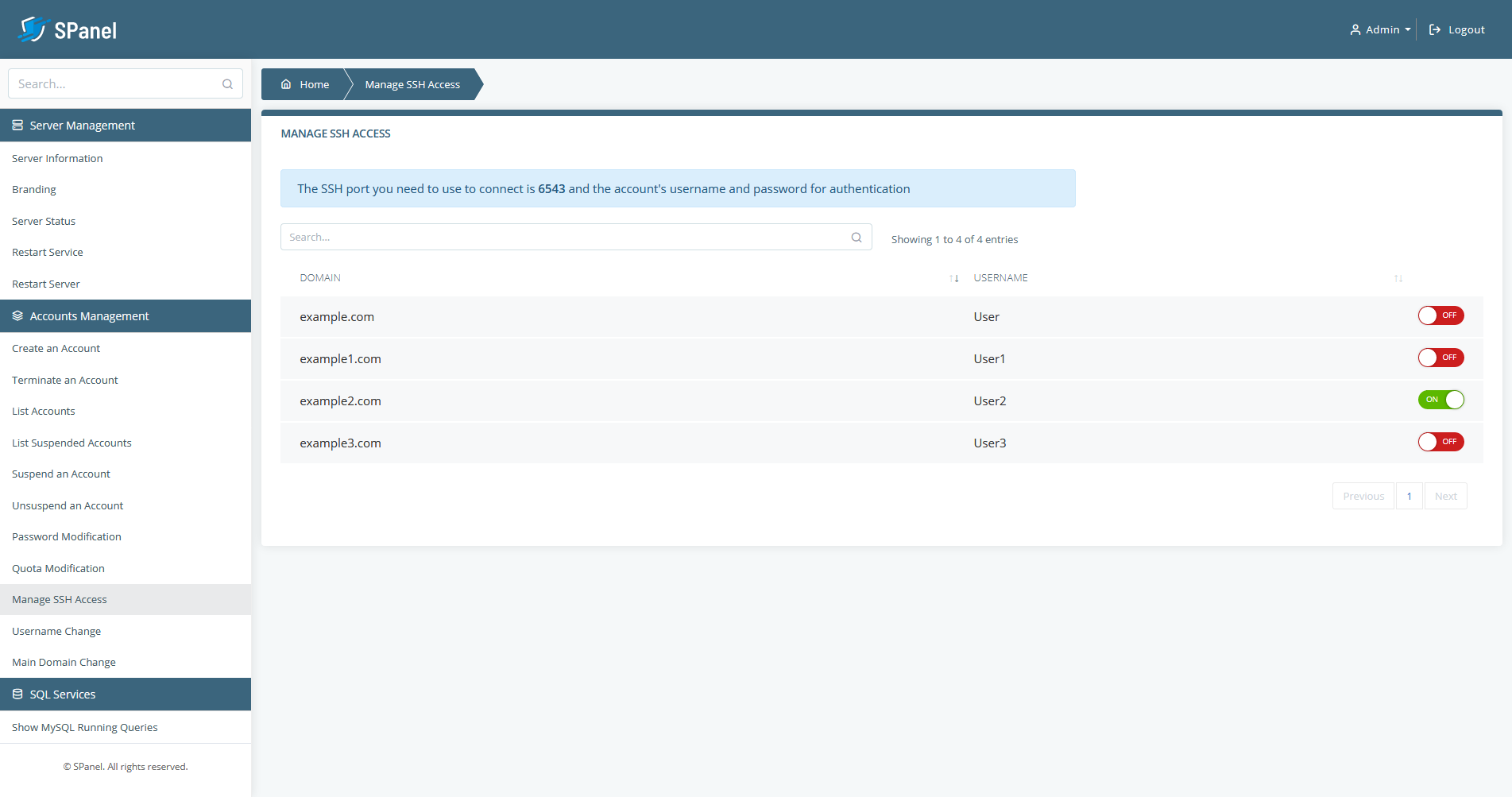
To do that, you need to go to Manage SSH Access under the Accounts Management panel. You’ll see the list of all accounts you’ve created, and alongside them, there are toggle switches through which you can manage their SSH access. Above the list, there’s a help box reminding you that SSH connections to ScalaHosting’s servers pass through port 6543 instead of the default port 22 and that users need to use their usernames and passwords in order to gain access.
If you’re initiating an SFTP session through a command-line interface, you need to use the following command:
sftp -p 6543 [username[@[the server’s hostname or IP]
You will be asked for your password, and after you’re successfully authenticated, you can use some of the following commands to perform various actions:
|
Command |
Function |
|
ls or dir |
List the contents of the current directory on the server |
|
cd |
Change the current directory on the server |
|
pwd |
Show the present working directory on the server |
|
put |
Upload a file to the server |
|
get |
Download a file from the server |
|
chmod |
Change the permissions on a file |
|
rename |
Rename a file on the server |
|
mkdir |
Create a directory on the server |
|
rm |
Delete a file from the server |
|
rmdir |
Delete an empty directory from the server |
|
exit |
Quit the session |
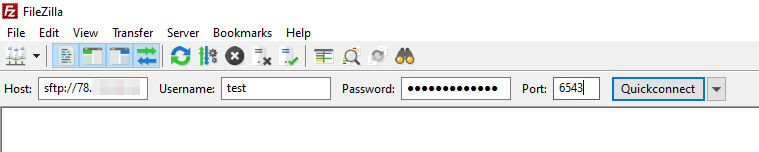
If you feel more comfortable logging into to your server through a Graphical User Interface (GUI), you can use an FTP client like FileZilla to establish your SFTP connection. The steps aren’t that different from the ones you take to set up a regular FTP session.
The only thing you need to do is enter sftp:// before the server’s IP in the host field and specify the SSH port (in the case of ScalaHosting’s managed VPSs, it’s 6543).
Conclusion
FTP has played a major role in the development of the internet, and it’s safe to say that without it, the online world would be a very different place. It wasn’t build with security in mind, however, and it can now put your entire online project at risk. Given the fact that you have alternatives like SFTP that are built on complex cryptographic algorithms, you have no excuse for using FTP.
